How to view the System Log on a Mac
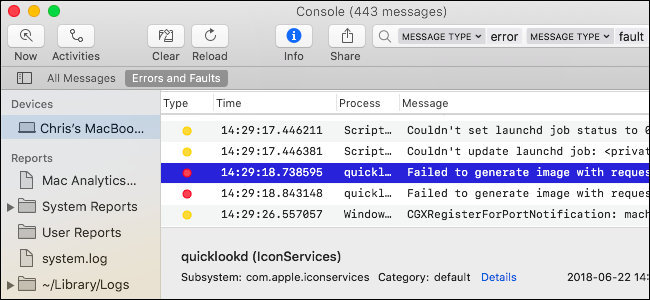
Your Mac keeps system logs, which can help diagnose and troubleshoot problems with macOS and your installed applications. These logs are stored as plain-text log files on your Mac’s system drive, and macOS also includes an app for viewing them.
[mai mult...]DEB Files on Arch? Run Any App on any Linux distro with this tool
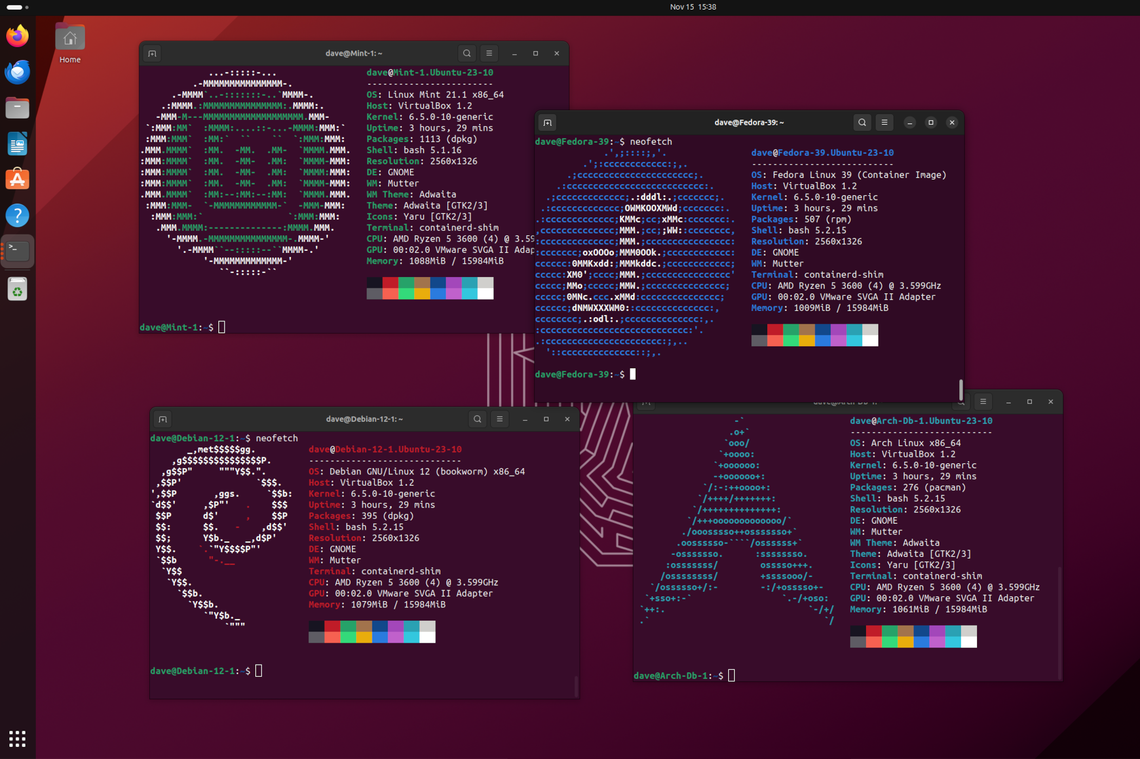
Frustrated by an app’s absent or lagging support for your preferred distro? Like magic, Distrobox runs applications from different Linux distributions right on your Linux computer. They’re running on your computer, yet they’re in their own native distribution.
[mai mult...]How to use the head Command on Linux
How to move your Linux home Directory to another Drive
How to use the traceroute Command on Linux
How to install the Windows Subsystem for Linux on Windows 11
To install the Windows Subsystem for Linux (WSL) on Windows 11, run Terminal as administrator, then enter “wsl –install” into the window. Run “wsl –install -d Distro”, replacing “Distro” with the name of a Linux distro, to install a specific distribution instead of Ubuntu. You can install additional Linux distros from the Terminal or the Microsoft Store.
The Windows Subsystem for Linux (WSL) lets you run Linux software on your Windows 11 PC. When you enable WSL, Windows will install a custom-built Linux kernel. You can then install Ubuntu or another Linux distribution of your choice.
[mai mult...]How to use the whois Command on Linux
A whois lookup will tell you a lot of information about who owns an internet domain. On Linux, you can run whois lookups from the command line. We’ll walk you through it.
[mai mult...]