Situatie
Solutie
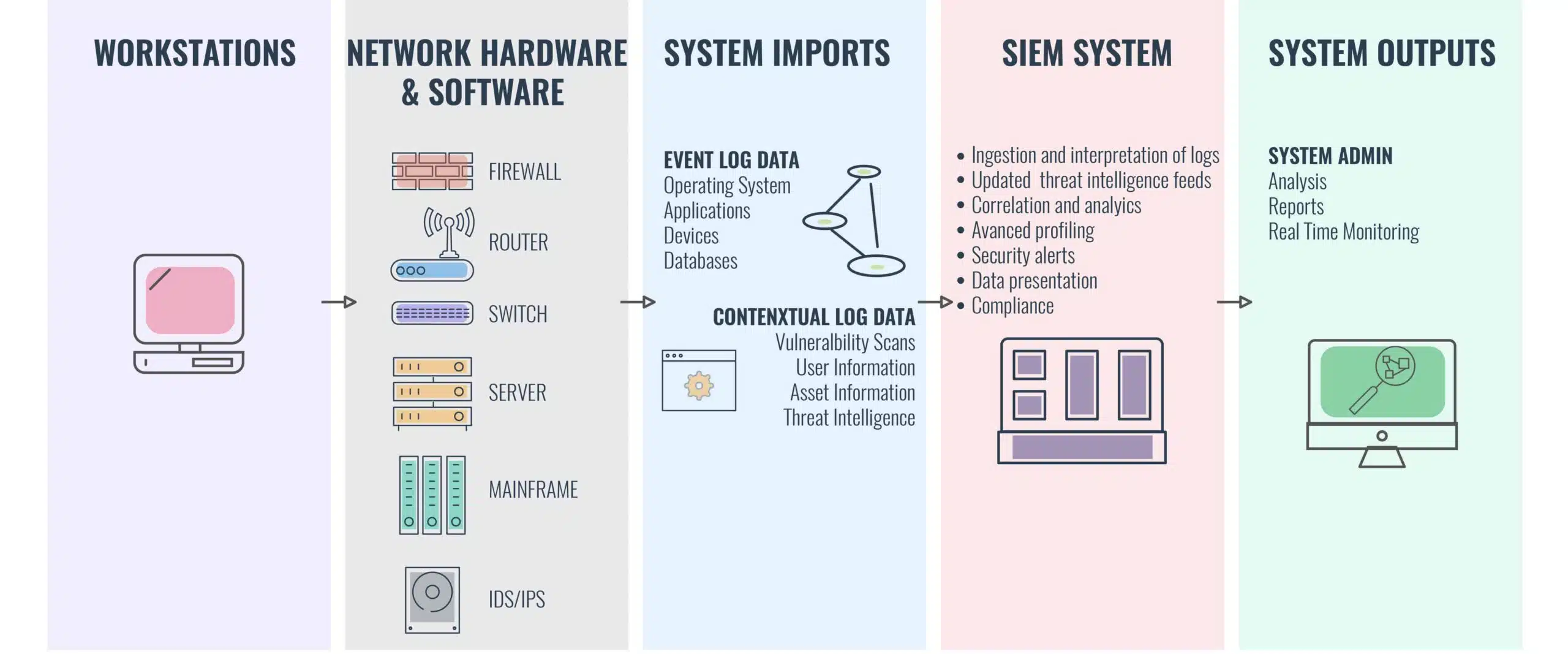
SIEM is an umbrella term for security software packages ranging from Log Management Systems to Security Log / Event Management, Security Information Management, and Security Event correlation. More often than not these features are combined for a 360-degree view.
While a SIEM system isn’t foolproof, it’s one of the key indicators that an organization has a clearly defined cybersecurity policy. Nine times out of ten, cyber attacks don’t have any clear tells on a surface level. To detect threats, it’s more effective to use the log files. The superior log management capabilities of SIEMs have made them a central hub of network transparency.
Most security programs operate on a micro-scale, addressing smaller threats but missing the bigger picture of cyber threats. An Intrusion Detection System (IDS) alone can seldom do more than monitor packets and IP addresses. Likewise, your service logs only show user sessions and configuration changes. SIEM puts these systems and others like it together to provide a complete overview of any security incident through real-time monitoring and the analysis of event logs.
Security Information and Event Management (SIEM) tools are an important component of log management and overall security. Here is a list of the best SIEM tools on the market for businesses wishing to expand or improve their solutions.
Through capabilities like log management and security information management, security information and event management, or SIEM, delivers insights into a business IT environment. While a SIEM system isn’t perfect, it is one of the most important indicators that a company has a well-defined cybersecurity policy. Cyber attacks, nine times out of ten, have no obvious tells on the surface. Using log files to detect threats is more effective. SIEMs have become a crucial hub of network transparency due to their superior log handling capabilities.
SIEM’s basic capabilities are as follows:
- Log Collection
- Normalization – Collecting logs and normalizing them into a standard format)
- Notifications and Alerts – Notifying the user when security threats are identified
- Security Incident Detection
- Threat response workflow – Workflow for handling past security events
SIEM records data from across a users’ internal network of tools and identifies potential issues and attacks. The system operates under a statistical model to analyze log entries. SIEM distributes collection agents and recalls data from the network, devices, servers, and firewalls.
All this information is then passed to a management console where it can be analyzed to address emerging threats. It’s not uncommon for advanced SIEM systems to use automated responses, entity behavior analytics and security orchestration. This ensures that vulnerabilities between cybersecurity tools can be monitored and addressed by SIEM technology.
Why SIEM: Critical Benefits?
Security information and event management solutions provide key threat-detection capabilities, real-time reporting, compliance tools, and long-term log analysis. The top benefits are:
- Increased security effectiveness and faster response to threats. To be useful, a security and event management solution must “enable an analyst to identify and respond to suspicious behavior patterns faster and more effectively than would be possible by looking at data from individual systems,”. To be truly effective, it must be able to prevent successful breaches.
- Efficient compliance demonstration. SIEM technology should also make it easy for SIEM IT teams to track and report compliance with industry and governmental regulations and security standards.
- Significant reduction in complexity. Consolidating security event data from multiple applications and devices enables fast and comprehensive analysis. In addition, repetitive tasks are automated and tasks that previously required experts can be performed by less experienced staff.
SIEM has become a core security component of modern organizations. The main reason is that every user or tracker leaves behind a virtual trail in a network’s log data. SIEM systems are designed to use this log data in order to generate insight into past attacks and events. A SIEM system not only identifies that an attack has happened, but allows you to see how and why it happened as well.
As organizations update and upscale to increasingly complex IT infrastructures, SIEM has become even more critical in recent years. Contrary to popular belief, firewalls and antivirus packages are not enough to protect a network in its entirety. Zero-day attacks can still penetrate a system’s defenses even with these security measures in place. SIEM addresses this problem by detecting attack activity and assessing it against past behavior on the network. A SIEM system has the ability to distinguish between legitimate use and a malicious attack. This helps to increase a system’s incident protection and avoid damage to systems and virtual property.
The use of SIEM also helps companies to comply with a variety of industry cyber management regulations. Log management is the industry-standard method of auditing activity on an IT network. SIEM systems provide the best way to meet this regulatory requirement and provide transparency over logs in order to generate clear insights and improvements.

Leave A Comment?