Situatie
Capturing a TCP 3-way handshake is a great way to learn how packets work. It shows you the basic process of how devices establish a reliable connection over the network, including key elements like sequence numbers, flags, and acknowledgments. By analyzing the handshake, you can better understand the flow of data in a TCP connection and how different parts of a packet contribute to establishing communication between devices. It’s a hands-on way to learn about networking fundamentals.
Solutie
1. Start Capturing Packets:
Open Wireshark and select the network interface you’re using. Click Start to begin capturing packets.
2. Initiate a TCP Connection:
Open a browser and connect to a server, like visiting a website. This will trigger the 3-way handshake between your device and the server.
3. Stop the Capture:
After you’ve triggered the connection and the handshake has occurred, click Stop in Wireshark to stop capturing further traffic.
4. Filter for TCP Handshake:
Apply the filter tcp in Wireshark to narrow down the traffic and focus on the handshake packets.
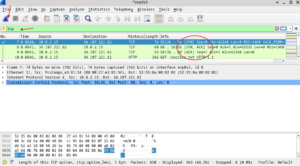
5. Analyze the 3-Way Handshake:
Now, look at the 3-way handshake:
- SYN: The client sends a SYN packet to initiate the connection.
- SYN-ACK: The server responds with a SYN-ACK packet to acknowledge the request.
- ACK: The client sends an ACK packet to confirm the connection.
6. Review the Details:
Click on each packet to inspect details like the sequence numbers, flags, and any other relevant information in the TCP headers.

Leave A Comment?