Situatie
SET (Social-Engineering Toolkit) is a powerful tool for simulating social engineering attacks like phishing and credential harvesting. It allows you to easily create fake login pages and test user awareness in a controlled environment. Useful for ethical hacking, security training, and penetration testing, SET helps assess vulnerabilities to real-world attacks. Always ensure it’s used responsibly and with proper authorization.
Important Reminder:
Only use this setup for ethical purposes, such as testing security awareness in environments where you have explicit permission. Phishing without authorization is illegal.
Solutie
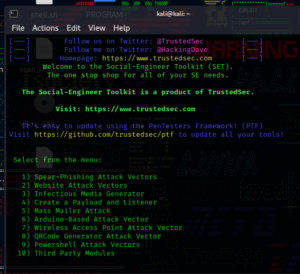
- Launch SET: Open a terminal in Kali Linux and run the following command:
sudo setoolkit - Select Social-Engineering Attack Vector: From the main menu, choose:
1) Social-Engineering Attacks - Choose Website Attack Vectors: Select:
2) Website Attack Vectors - Select Credential Harvester Attack Method: Choose:
3) Credential Harvester Attack Method - Select Site Cloner: Choose:
2) Site Cloner - Enter Your Local IP Address: You will be prompted to provide the IP address where the phishing page will be hosted. Find your local IP using:
ifconfigEnter the IP address (e.g.,192.168.1.100). - Enter the Target Website URL: Provide the URL of the site you want to clone (e.g.,
https://example.com). SET will download the HTML and necessary files to mimic the website. For example, if testing awareness, you might clone:- A login portal
- A corporate intranet login page
- Hosting the Fake Page: SET will automatically host the fake login page using your local IP. Example:
Credential Harvester is running on http://192.168.1.100 - Test the Fake Login Page: Open a browser on another device in the same network and visit
http://192.168.1.100. Enter credentials in the fake login form. - Monitor Credential Harvesting: Any credentials entered on the fake page will appear in the SET terminal in real-time.

Leave A Comment?