How to reset your router to restore factory default settings
It’s important to note that when you reset your home router you will lose all of your current network settings, like the name of the Wi-Fi network, its password, etc
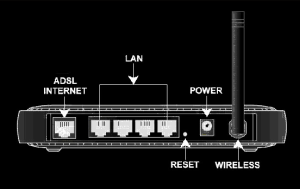
How to Reset a Router
- Keep your router plugged in.
- Find your router’s reset button. This will be on the back or the bottom of your router.
- Use a paperclip to hold down the reset button for 10-15 seconds.
- Release the button.
- Wait for the router to power back on.
- On many routers, if you hold in the button for 10 seconds, it factory resets your router.
Should i reset my router to factory settings?
Routers, like computers, work best with regular hard resets. Resetting a router can also clear the memory, which is critical for those with multiple devices or an older router. Resetting your router is an easy way to prevent malware attempts – the FBI even recommends router resets for that reason.
How often should you reset your router?
Know when to reboot your router so you can maintain a healthy, speedy internet connection. A good rule of thumb is to reboot your router or wireless gateway once a month to clear out its memory and refresh your wired and wireless connections or just when you have issues with it.