Situatie
Solutie
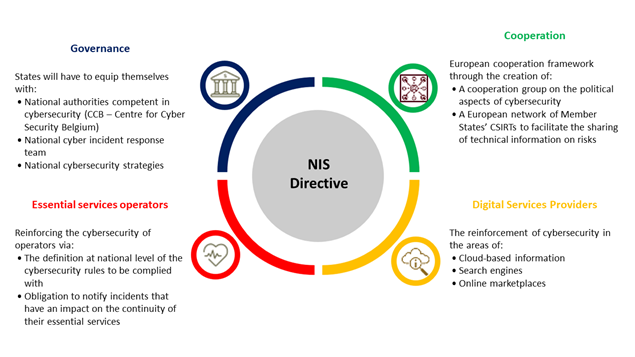
This directive defines a set of network and information security requirements that apply to “Digital Service Providers” (DSPs) and “Operators of Essential Service” (OESs). It concerns companies in the energy, transport, banking, financial markets, health, drinking water distribution and digital infrastructure sectors. Companies that are not included in this scope will be able to take note of it if their suppliers and partners are affected by these obligations.
What is at stake with NIS directive?
The European NIS Directive highlights 4 major issues:
What should companies do, specifically?
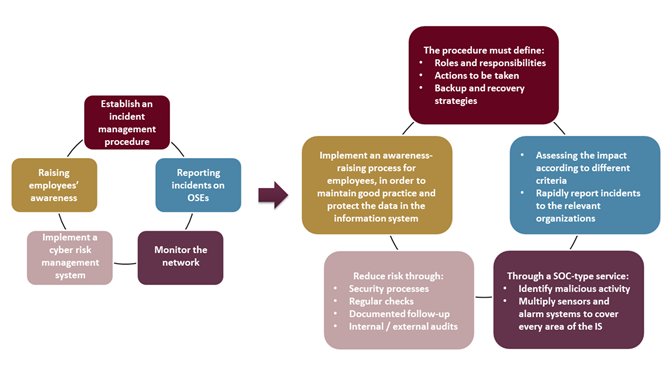
Stakeholders affected by this directive must, as part of their projects to comply and improve their overall security, implement 5 key measures:
What are the limitations of the NIS Directive?
Nevertheless, the decree leaves some grey areas. We can highlight:
- The list of IS not subject to mapping and declaration
- The depth and duration of annual audits
- The acceptable level of alerts
Some measures of this Directive may already be defined in other reference systems. It is therefore necessary to adapt them according to the environment and the information system, but they should not be weakened in any way. For example, the governance aspect already imposed by the HAS (Haute Autorité de Santé – French National Authority for Health) certification, the obligation to report incidents or the reporting of indicators.
Cyber Resilience for Critical Infrastructure means removing privileges to prevent Ransomware
The NIS Directive calls for subjects to “Build resilience against cyber attacks” and recent events highlight critical places to start.
Ransomware epidemics, such as WannaCry and NotPetya, caused havoc across the globe and highlight the vulnerability of the healthcare vertical, which has been reliant on legacy, vulnerable systems with little to no cyber resilience in place.
The idealist advice of replacing legacy systems and enhancing user awareness is simply not practical, especially for those in the UK who run healthcare technology that requires legacy operating systems.
A more practical and realistic approach has emerged in recent years: endpoint privilege management can ensure cyber resilience by removing the privileges that ransomware requires to run.
Endpoint privilege management is a key component of PAM that enables businesses to painlessly implement intelligent application white, black, and restricting policies across their business, and then remove local admin rights to ensure resilience against malware.

Leave A Comment?