Situatie
Solutie
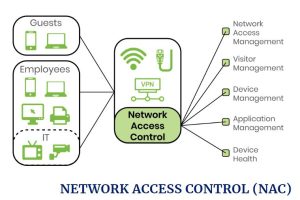
Network Access Control (NAC) is the act of keeping unauthorized devices (and their users) out of your private network. Organizations that give certain devices unmanaged devices access to your network via network access control but only if these devices meet organizational security compliance checks. Those checks can include:
- Patch status
- AV, EDR, or anti-malware present and functioning
- Grant or deny permissions (aid with zero-trust model)
- require 2FA to pass NAC security checks
NAC is a generic term for a solution that selectively grants network access to devices based on one or more criteria. Those criteria could be based on authentication (only authorized users are granted access to the network), security posture (only devices with up-to-date operating systems and antivirus software can connect), or any number of other criteria (device manufacturer, employee access level, etc).
Modern NAC solutions can be both flexible and powerful, with policy-based enforcement allowing for very granular but still scalable levels of access control. NAC security can be applied to both wired and wireless networks.
What is the importance of network access control?
NAC is critical for modern businesses because it allows organizations to monitor the devices and users — authorized and unauthorized — trying to access the network.
Unauthorized users include cybercriminals, hackers and data thieves, and other bad actors that an organization must keep out. But businesses must also be gatekeepers for authorized users. This particularly applies to organizations that allow remote access to the enterprise network from non-corporate devices like mobile phones, laptops and tablets, or companies that allow employees working in the office to use personal devices. Both scenarios create security risks demanding organizations to address network security.
NAC is one aspect of network security. It provides visibility into the devices and users trying to access the enterprise network. And it controls who can access the network, including denying access to those users and devices that don’t comply with security policies. NAC solutions and tools help companies control network access, ensure compliance and strengthen their IT infrastructure.
The 802.1X NAC operation sequence is as follows:
1. Initiation—The authenticator (typically a switch) or supplicant (client device) sends a session initiation request. A supplicant sends an EAP-response message to the authenticator, which encapsulates the message and forwards it to the authentication server.
2. Authentication—Messages pass between the authentication server and the supplicant via the authenticator to validate several pieces of information.
3. Authorization—If the credentials are valid, the authentication server notifies the authenticator to give the supplicant access to the port.
4. Accounting—RADIUS accounting keeps session records including user and device details, session types, and service details.
5. Termination—Sessions are terminated by disconnecting the endpoint device, or by using management software.
Many of the top network access control benefits come from policies. Rather than manually approve/deny access on a per-device or user basis, a network or system admin can define the conditions that are necessary for access. NAC isn’t necessarily all-or-nothing, and more advanced policies might grant guests or contractors a different level of network access than full-time employees. Devices can also be “quarantined,” giving them just enough access to update software or take other corrective action without allowing them to touch the rest of the internal network.

Leave A Comment?