How to compile and install Linux Kernel 5.16.9
The procedure to build (compile) and install the latest Linux kernel from source is as follows:
- Grab the latest kernel from kernel.org
- Verify kernel
- Untar the kernel tarball
- Copy existing Linux kernel config file
- Compile and build Linux kernel 5.16.9
- Install Linux kernel and modules (drivers)
- Update Grub configuration
- Reboot the system
Step 1. Get the latest Linux kernel source code
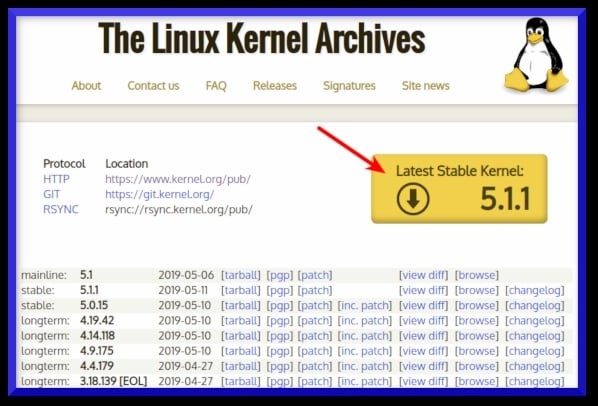
Visit the official project site and download the latest source code. Click on the big yellow button that read as “Latest Stable Kernel“:
The filename would be linux-x.y.z.tar.xz, where x.y.z is actual Linux kernel version number. For example file linux-5.16.9.tar.xz represents Linux kernel version 5.16.9. Use the wget command to download Linux kernel source code:
$ wget https://cdn.kernel.org/pub/linux/kernel/v5.x/linux-5.16.9.tar.xz
Step 2. Extract tar.xz file
You really don’t have to extract the source code in /usr/src. You can extract the source code in your $HOME directory or any other directory using the following unzx command or xz command:
$ unxz -v linux-5.16.9.tar.xz
OR
$ xz -d -v linux-5.16.9.tar.xz
Verify Linux kernel tartball with pgp
First grab the PGP signature for linux-5.16.9.tar:
$ wget https://cdn.kernel.org/pub/linux/kernel/v5.x/linux-5.16.9.tar.sign
Try to verify it:
$ gpg --verify linux-5.16.9.tar.sign
Sample outputs:
gpg: assuming signed data in 'linux-5.16.9.tar' gpg: Signature made Sun 12 Aug 2018 04:00:28 PM CDT gpg: using RSA key 79BE3E4300411886 gpg: Can't check signature: No public key
Grab the public key from the PGP keyserver in order to verify the signature i.e. RSA key ID 79BE3E4300411886 (from the above outputs):
$ gpg --recv-keys 79BE3E4300411886
Sample outputs:
gpg: key 79BE3E4300411886: 7 duplicate signatures removed gpg: key 79BE3E4300411886: 172 signatures not checked due to missing keys gpg: /home/vivek/.gnupg/trustdb.gpg: trustdb created gpg: key 79BE3E4300411886: public key "Linus Torvalds <torvalds@kernel.org>" imported gpg: no ultimately trusted keys found gpg: Total number processed: 1 gpg: imported: 1
Now verify gpg key again with the gpg command:
$ gpg --verify linux-5.16.9.tar.sign
Sample outputs:
gpg: assuming signed data in 'linux-5.16.9.tar' gpg: Signature made Sun 12 Aug 2018 04:00:28 PM CDT gpg: using RSA key 79BE3E4300411886 gpg: Good signature from "Linus Torvalds <torvalds@kernel.org>" [unknown] gpg: aka "Linus Torvalds <torvalds@linux-foundation.org>" [unknown] gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: ABAF 11C6 5A29 70B1 30AB E3C4 79BE 3E43 0041 1886
If you do not get “BAD signature” output from the “gpg –verify” command, untar/extract the Linux kernel tarball using the tar command, enter:
$ tar xvf linux-5.16.9.tar
Step 3. Configure the Linux kernel features and modules
Before start building the kernel, one must configure Linux kernel features. You must also specify which kernel modules (drivers) needed for your system. The task can be overwhelming for a new user. I suggest that you copy existing config file using the cp command:
$ cd linux-5.16.9
$ cp -v /boot/config-$(uname -r) .config
Sample outputs:
'/boot/config-4.15.0-30-generic' -> '.config'
Step 4. Install the required compilers and other tools
You must have development tools such as GCC compilers and related tools installed to compile the Linux kernel.
How to install GCC and development tools on a Debian/Ubuntu Linux
Type the following apt command or apt-get command to install the same:
$ sudo apt-get install build-essential libncurses-dev bison flex libssl-dev libelf-dev
How to install GCC and development tools on a CentOS/RHEL/Oracle/Scientific Linux
Try yum command:
$ sudo yum group install "Development Tools"
OR
$ sudo yum groupinstall "Development Tools"
Additional packages too:
$ sudo yum install ncurses-devel bison flex elfutils-libelf-devel openssl-devel
How to install GCC and development tools on a Fedora Linux
Run the following dnf command:
$ sudo dnf group install "Development Tools"
$ sudo dnf install ncurses-devel bison flex elfutils-libelf-devel openssl-devel
Step 5. Configuring the kernel
Now you can start the kernel configuration by typing any one of the following command in source code directory:
- $ make menuconfig – Text based color menus, radiolists & dialogs. This option also useful on remote server if you wanna compile kernel remotely.
- $ make xconfig – X windows (Qt) based configuration tool, works best under KDE desktop
- $ make gconfig – X windows (Gtk) based configuration tool, works best under Gnome Dekstop.
For example, run make menuconfig command launches following screen:
$ make menuconfig

Start compiling and tocreate a compressed kernel image, enter:
$ make
To speed up compile time, pass the -j as follows:
## use 4 core/thread ##
$ make -j 4
## get thread or cpu core count using nproc command ##
$ make -j $(nproc)
Compiling and building the Linux kernel going take a significant amount of time. The build time depends upon your system’s resources such as available CPU core and the current system load. So have some patience.
Install the Linux kernel modules
$ sudo make modules_install
Install the Linux kernel
So far we have compiled the Linux kernel and installed kernel modules. It is time to install the kernel itself:
$ sudo make install
It will install three files into /boot directory as well as modification to your kernel grub configuration file:
- initramfs-5.16.9.img
- System.map-5.16.9
- vmlinuz-5.16.9
Step 6. Update grub config
You need to modify Grub 2 boot loader configurations. Type the following command at a shell prompt as per your Linux distro:
CentOS/RHEL/Oracle/Scientific and Fedora Linux
$ sudo grub2-mkconfig -o /boot/grub2/grub.cfg
$ sudo grubby --set-default /boot/vmlinuz-5.16.9
You can confirm the details with the following commands:
grubby --info=ALL | more
grubby --default-index
grubby --default-kernel
Debian/Ubuntu Linux
The following commands are optional as make install does everything for your but included here for historical reasons only:
$ sudo update-initramfs -c -k 5.16.9
$ sudo update-grub
How to build and install the latest Linux kernel from source code
You have compiled a Linux kernel. The process takes some time, however now you have a custom Linux kernel for your system. Let us reboot the system.
Just issue the reboot command or shutdown command:
# reboot
Verify new Linux kernel version after reboot:
$ uname -mrs
Sample outputs:
Linux 5.16.9 x86_64[mai mult...]