Situatie
Solutie
Also known as SIM splitting, simjacking, SIM hijacking, and port-out scamming, SIM swapping is a type of fraud that targets your personal information so that cybercriminals can pass themselves off as you and access your bank accounts. In short, the fraud takes aim at moving control of someone’s phone account from their SIM card to one controlled by the hacker. In general, most victims don’t know they’ve been compromised until they try to place a call or send a text message which doesn’t go through.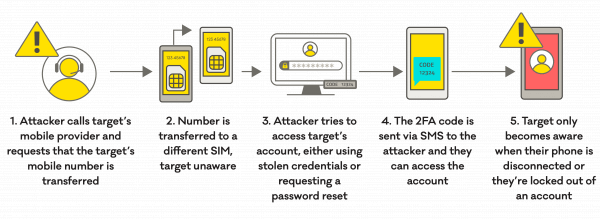
What is SIM swapping attack?
In a SIM swapping attack, an attacker takes over the mobile phone number of the real subscriber, by asking the mobile telecom provider to link that number to a SIM card under the attacker’s control. SIM swapping procedures exist for legitimate reasons, for instance, when the SIM card is lost or damaged. SIM swapping is also used to connect mobile phones with an embedded SIM (eSIM). eSIMs are increasingly common.
In a SIM swapping attack, the attacker will convince the telecom provider to do the SIM swap, using social engineering techniques, pretending to be the real customer, claiming that the original SIM card is for example damaged or lost. When the attack is successful, the genuine subscriber’s phone will lose connection to the network and they won’t be able to make or receive phone calls.
How does a SIM swapping attack happen?
The attacker typically begins a SIM swapping attack by gathering personal details about the targeted subscriber. There are many ways personal data can be retrieved, this can be done through social engineering, phishing, malware, exploiting information from data breaches or doing research on social media.
Having all necessary information, the attacker would be able to convince the mobile network operator to transfer the subscriber’s mobile number to a new SIM card under their control, or perform the process themselves online.
As a result, the attacker takes over the account and can receive all the SMS and voice calls intended for the legitimate subscriber. Fraudsters can perform online banking frauds but can also bypass the two-factor authentication (2FA) used to secure social media and other online accounts.
Why do these attack take place?
Specific circumstances may open the opportunity for attackers, which can be:
- Weak customer authentication processes;
- Negligence or lack of cyber training or hygiene;
- Lack of risk awareness.
How to protect yourself from a SIM card swap attack:
- Never reply to calls, emails, or text messages that ask for your personal information. They’re most likely phishing attempts by scammers looking to get personal information to access your mobile phone, bank account, social media, or other accounts. If by any chance you get such a request, you should try to contact that particular company using through an official phone number or website.
- Mark my words: you should limit the personal information you share online as much as you can. Avoid disclosing your full name, sharing your address, or phone number on public websites. There’s nothing easier for an identity thief to track down that content, use it to answer the security questions required to authenticate your identity, and log in to your personal accounts.
- Always set up a PIN or password with your service provider to access your phone for any online or phone interactions. This way, you can help protect your account from unauthorized changes. You can always check for more details on how to do this on your provider’s website.
- Never use the same passwords/PINs/usernames over multiple accounts. Instead, create a strong, unique password for your sensitive personal/financial accounts. For more actionable tips on this subject,

Leave A Comment?