Microsoft Store Error Code 0xC002001B
Înainte de a începe cu soluțiile ușor complexe, încercați mai întâi acestea rapide:
- Verificați dacă există actualizări Windows în așteptare și instalați-le.
- Asigurați-vă că ați setat data și ora corecte pe computer.
- Dacă întâmpinați probleme cu Microsoft Intune ( Portalul companiei ), asigurați-vă că rețeaua dvs. nu blochează accesul la Microsoft Store. Introducerea pe lista albă a MS Store în Zscaler a făcut trucul pentru mulți.
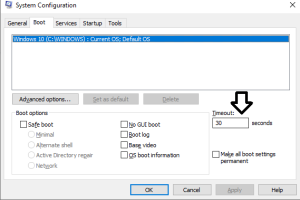
1. Descărcați manual patch-ul KB5015020 (Windows 10)
- Accesați Catalogul Microsoft Update și faceți clic pe linkul Descărcare de lângă versiunea KB5015020 și arhitectura care se potrivește cu instalarea actuală.
- După ce ați terminat, faceți dublu click pe fișierul MSU descărcat .
- Așteptați să se încarce configurarea și urmați instrucțiunile de pe ecran pentru a finaliza procesul de instalare.
Actualizarea cumulativă KB5015020 pentru Windows 10, versiunea 22H2, a remediat codul de eroare Microsoft Store 0xC002001B pentru majoritatea. Dar rețineți că nu funcționează pe Windows 11.
2. Goliți memoria cache și rulați serviciile critice
- Apăsați Windows+ R pentru a deschide Run, tastați wsreset.exe în câmpul de text și apăsați Enter.
- Apoi, apăsați Windows+ Epentru a deschide File Explorer , navigați pe următoarea cale sau inserați-o în bara de adrese și apăsați Enter:
C:\Windows\SoftwareDistribution\Download - Apăsați Ctrl+ A pentru a selecta toate fișierele și apoi apăsați Delete pentru a le șterge.
- Alegeți răspunsul adecvat în cazul în care apare o solicitare de confirmare.
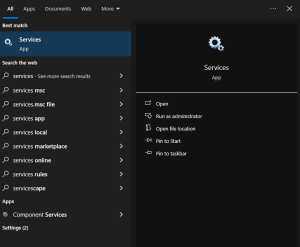
- Acum, apăsați Windows+ S pentru a deschide Căutare , tastați Servicii în bara de căutare și faceți click pe rezultatul căutării relevante.
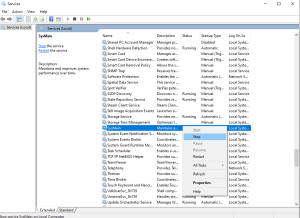
- Faceți click dreapta pe Microsoft Store Install Service și selectați Proprietăți din meniul contextual.
- Selectați Automat din meniul drop-down Tip de pornire și faceți click pe butonul Start pentru a rula serviciul.
- În cele din urmă, faceți click pe Aplicare și OK pentru a salva modificările.
3. Reparați fișierele de sistem corupte
- Apăsați Windows+ Rpentru a deschide Run , tastați cmd și apăsați Ctrl+ Shift+ Enter.
- Faceți click pe Da în promptul UAC
- Lipiți următoarele comenzi DISM individual și apăsați Enterdupă fiecare:
DISM /Online /Cleanup-Image /CheckHealth
DISM /Online /Cleanup-Image /ScanHealth
DISM /Online /Cleanup-Image /RestoreHealth
4. Acum, executați această comandă pentru scanarea SFC:sfc /scannow
5.În cele din urmă, reporniți computerul pentru ca modificările să se aplice.
[mai mult...]