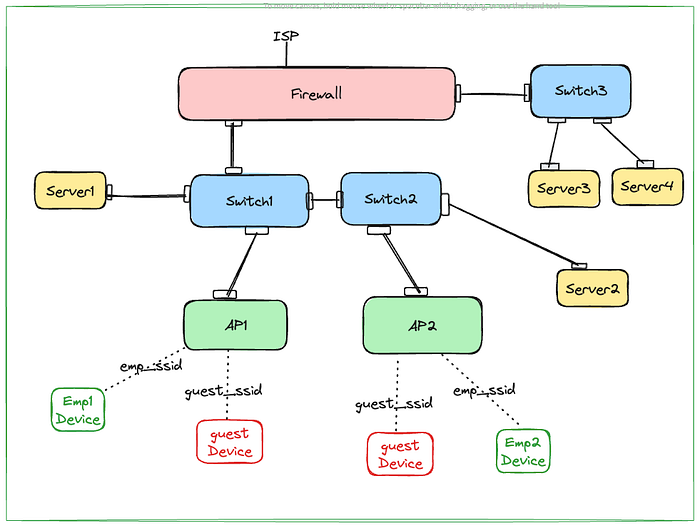
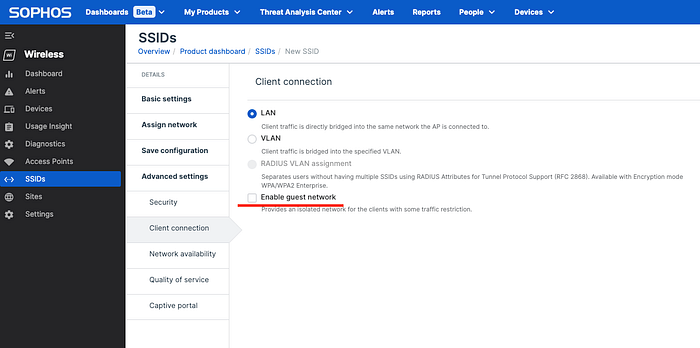
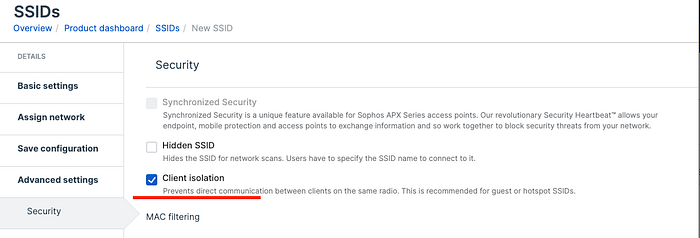
Pi-hole on Raspberry Pi: complete Installation & Configuration Guide
Pi-hole is a network-wide ad blocker that acts as a DNS sinkhole. By running it on a Raspberry Pi, you can block ads and trackers for all devices on your network without needing browser extensions.
[mai mult...]